We Monitor, Hunt and
Mitigate Cyber Crimes
With Real Intelligence
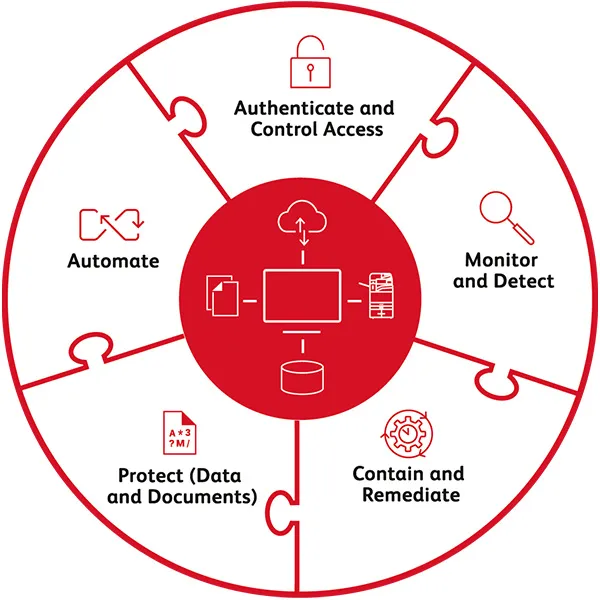
We help organizations embrace zero trust.
What we do
Consulting Services

Red Teaming and Adversary Simulation
Uncover vulnerabilities before attackers do with our cutting-edge red teaming services.

Web Application Security Testing
Perform thorough web application security testing to uncover and fix vulnerabilities, ensuring robust protection against potential data breaches.

Compliance & Audit
Ensure regulatory compliance and security through detailed compliance and audit services, adhering to industry standards and mitigating risks.

Elite OT/ICS Cybersecurity Assessment
Secure your aviation infrastructure with Sudosafe' advanced OT and ICS cybersecurity assessments. We ensure top-tier protection for critical airport systems using globally recognized standards.

Security Consulting
Our elite team of cybersecurity experts stands ready to identify and neutralize threats before they can compromise your systems.

Specialized trainings
Learn the Art of Offensive Operations, Ethical Hacking, Penetration Testing, and more with our comprehensive training courses
providing us with reliable protection and peace of mind."
Healthcare Clint
providing us with reliable protection and peace of mind."
Healthcare Clint
providing us with reliable protection and peace of mind."
Healthcare Clint
providing us with reliable protection and peace of mind."
Healthcare Clint

